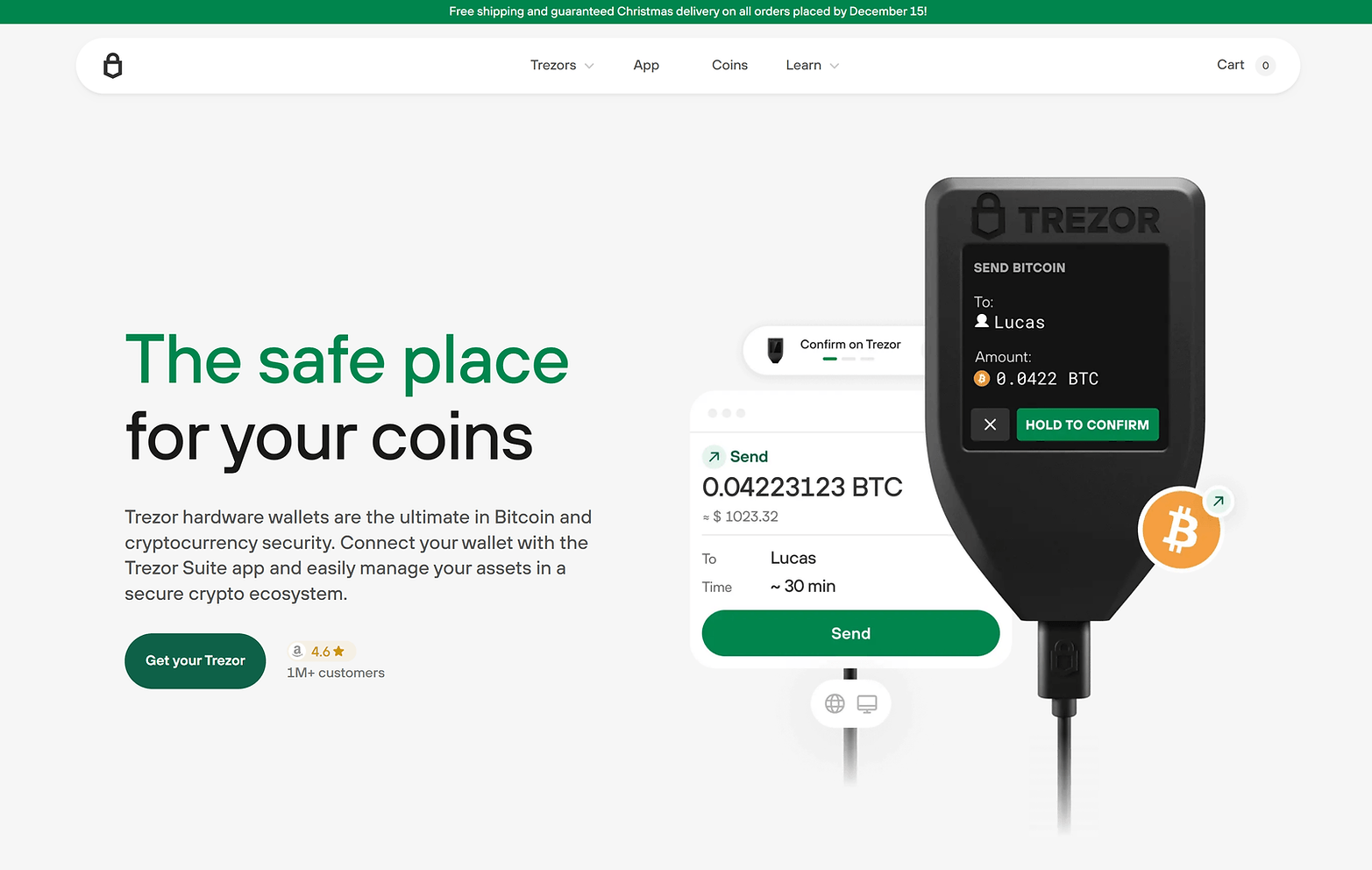
Trezor.io/start: Your Guide to Securing Cryptocurrency
In the rapidly evolving world of cryptocurrency, security is paramount. Trezor, a pioneer in hardware wallets, provides a secure solution to store and manage your digital assets. The first step to unlocking the full potential of your Trezor device is visiting trezor.io/start. This comprehensive guide will take you through everything you need to know about setting up your Trezor wallet, understanding its features, and ensuring your crypto investments are protected.
What is Trezor?
Trezor is a hardware wallet designed to provide the highest level of security for cryptocurrency users. Unlike software wallets that reside on your phone or computer and are vulnerable to hacks and malware, Trezor stores your private keys offline, making it nearly impossible for hackers to access your funds. Trezor supports a wide range of cryptocurrencies, including Bitcoin, Ethereum, and many others.
Why Visit Trezor.io/start?
The official Trezor website provides a dedicated portal at trezor.io/start to guide new users through the setup process. By visiting this link, users can:
-
Download the Trezor Suite, the official desktop and web app for Trezor.
-
Learn step-by-step instructions to initialize their Trezor device.
-
Access educational resources about cryptocurrency security.
-
Verify device authenticity to prevent counterfeit devices.
Setting Up Your Trezor Wallet
Setting up a Trezor wallet through trezor.io/start is straightforward, even for beginners. The steps include:
-
Connect Your Trezor Device: Plug in your Trezor to your computer or mobile device using the included USB cable.
-
Visit Trezor.io/start: Open your browser and navigate to trezor.io/start. Follow the on-screen instructions.
-
Install Trezor Suite: Download and install Trezor Suite for your operating system. This app will allow you to manage your cryptocurrencies securely.
-
Initialize Your Device: Choose whether you want to create a new wallet or recover an existing one. The initialization process will guide you through generating a recovery seed.
-
Backup Recovery Seed: Write down your recovery seed on the provided card. This step is critical—without it, you cannot recover your funds if the device is lost or damaged.
-
Set a PIN Code: Add an additional layer of security by setting a PIN code. This PIN is required every time you access your Trezor.
Security Features of Trezor
Trezor devices are built with advanced security features that protect your cryptocurrency investments. Some key aspects include:
-
Offline Storage: Your private keys never leave the device, keeping them safe from online attacks.
-
Recovery Seed: A 24-word recovery phrase allows you to restore access to your wallet in case of loss.
-
PIN Protection: A personalized PIN adds an extra layer of security against unauthorized access.
-
Passphrase Support: For even greater security, users can add a passphrase to their recovery seed.
-
Device Verification: Every Trezor device can be verified through the official website, ensuring authenticity.
Using Trezor Suite
Once your device is set up through trezor.io/start, you can manage all your crypto assets with Trezor Suite. This software provides a simple interface to:
-
Send and receive cryptocurrency safely.
-
Check your balance across multiple cryptocurrencies.
-
Exchange one cryptocurrency for another through integrated exchanges.
-
Track transaction history and portfolio performance.
Best Practices for Trezor Users
To maximize the security of your Trezor wallet, consider the following best practices:
-
Always download Trezor Suite from trezor.io/start or official sources.
-
Never share your recovery seed or PIN with anyone.
-
Keep your recovery seed stored securely, preferably offline in a safe location.
-
Regularly update your Trezor firmware to benefit from the latest security enhancements.
-
Be cautious of phishing attempts. Always verify URLs and email sources before entering sensitive information.
Common Issues and Troubleshooting
Even with the user-friendly design of Trezor, some issues may arise. Visiting trezor.io/start provides access to troubleshooting guides and FAQs. Common problems include:
-
Device not recognized by the computer.
-
PIN entry errors.
-
Recovery seed recovery difficulties.
-
Firmware update failures.
Following the official guide ensures that these issues can be resolved safely without compromising your crypto assets.
Why Trezor is Trusted by Crypto Enthusiasts
Trezor is widely recognized in the crypto community for its robust security, reliability, and user-friendly interface. Millions of users trust Trezor devices to protect their investments, and the company continuously updates its products to meet the highest security standards. Starting your journey at trezor.io/start ensures that you follow the most secure and official setup process.
Conclusion
For anyone looking to secure their cryptocurrency assets, a Trezor hardware wallet is one of the safest options. Visiting trezor.io/start is the first step toward a secure and well-managed crypto portfolio. From setting up your device to using Trezor Suite, this portal provides all the necessary resources to make your crypto journey safe and seamless. Remember, in the world of digital assets, security is everything, and Trezor is committed to keeping your investments protected.
Whether you are new to cryptocurrency or an experienced investor, trezor.io/start is the ultimate starting point for your Trezor experience. Take control of your digital assets today and ensure they remain secure for years to come.